
Reflected XSS on Error Page
Sometimes to exploit an XSS (specifically Reflected XSS), we are focused on finding input pages such as Search Columns, etc to find out is that form has an XSS vulnerability or not.
Not infrequently, a developer is only focused on doing sanitation and filters on these attacks on pages that visitors commonly visit. It does not rule out the possibility of XSS attacks can be affected on other pages, including an Error Pages.
When doing some Private Bug Hunting on Bugcrowd, I found a feature for Uploading and Downloading file. After the file is being uploaded successfully, to download the file, the user will be directed to the URL like this:
https://b15.[redacted.com]/file.php?spaceid=user@mail.com&file=filename.jpg
I. Testing Local File Read
At first, I thought the URL had an LFI or LFD vulnerability, but after trying to change the file parameters with another file, it didn't work and gave an error message.
https://b15.[redacted.com]/file.php?spaceid=&file=../../../../etc/passwd
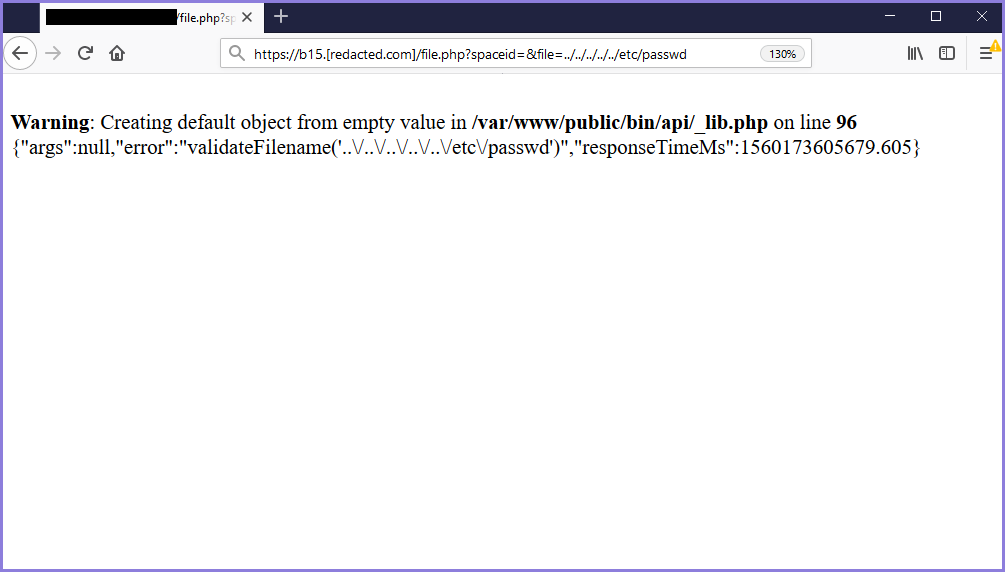
Figure 1 - Test for Local File Read and Failed
II. Testing HTML Ijection
But if you pay attention, the contents of the file parameter are reflected on the error page. Then I tried to insert an HTML tag to test whether there is a filter or not in the parameters of the file.
And sure enough, HTML tags were successfully rendered on that page.
https://b15.[redacted.com]/file.php?spaceid=&file=<h1>asu

Figure 2 - Test with HTML Injection Payload and Worked
III. Testing XSS
Without waiting a long time, I immediately tried an XSS payload on the page, and XSS was executed!
https://b15.[redacted.com]/file.php?spaceid=&file=<img src=x onmouseover=alert(1)>
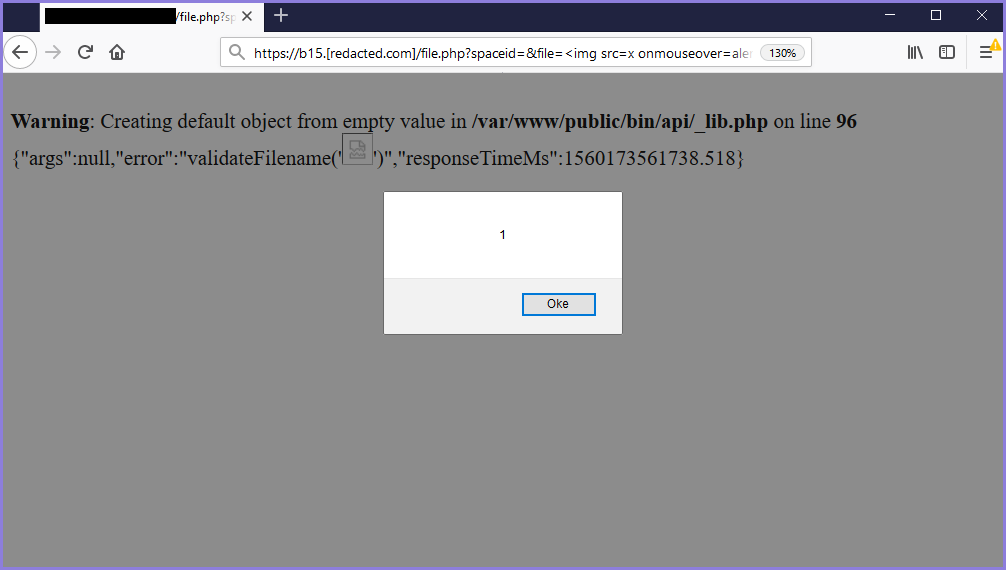
Figure 3 - Test with XSS Payload and Worked
Some tips for hunting Reflected XSS is to test various parameters contained in an endpoint. Either on the Front End Page or even on the Error Page like the example above.
So this article was written. Hopefully, it will be useful for us all.